
Conti Ransomware: Behavior and Techniques
Introduction
- T1082 - System Information Discovery
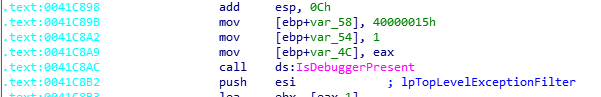

- T1497 - Virtualization/Sandbox Evasion

- T1027 - Obfuscated Files or Information
- T1543 - Create or Modify System Process

- T1490 - Inhibit System Recovery

- T1486 - Data Encrypted for Impact

The Microsoft Windows native CRYPTSP API is used to generate a different encryption key per file, with an RSA-4096 public encryption key unique for each victim. The ".mabdg" file extension is added to the encrypted files. In each traversed directory, the malware writes the ransom note named ‘readme.txt’ shown below.

Conclusion