
Breaking Down CVE-2021-4044: Microsoft MSHTML Vulnerability
What is CVE-2021-40444?
In short, CVE-2021-40444 is a critical vulnerability in Windows MSHTML that enables attackers to execute remote commands on a victim's machine using malicious Microsoft Office documents. There are several ways through which this vulnerability may be exploited. One attack uses a Docx file to achieve remote code execution, while the other uses an RTF file.
In this article, we're focusing on the first scenario. Here's what it can look like.
An attacker creates a specially-crafted Docx file with an ActiveX control that references public resources. Once opened by an unsuspecting victim, the document can be abused to execute malicious code while it is being loaded.
Granted, Microsoft considers files downloaded from the Internet to be dangerous, and Microsoft Office normally opens them in Protected View or Application Guard. In theory, this should mitigate the attack before it ever gets started. However, there are several ways around this — each of which could potentially enable attackers to succeed:
- The attacker is able to convince the victim to bypass the mitigations through social engineering.
- The victim ignores the Protected View warning.
- The document is delivered in an archived form.
How Does the Attack Work?
MSHTML is Microsoft’s proprietary browser engine for Internet Explorer and the default web rendering engine for Office. ActiveX is a deprecated programming framework no longer supported for Microsoft Edge, but is still supported for Internet Explorer.
In the example above, the malicious Docx file contains an ActiveX control that references public resources. Once the document is opened, MSHTML is activated (because of the web-based content), which will then use ActiveX to render the content. An archive file (CAB) is downloaded, and a dynamic-link library (DLL) is extracted from that, leading to remote code execution.
First, a request to an HTML file is made:
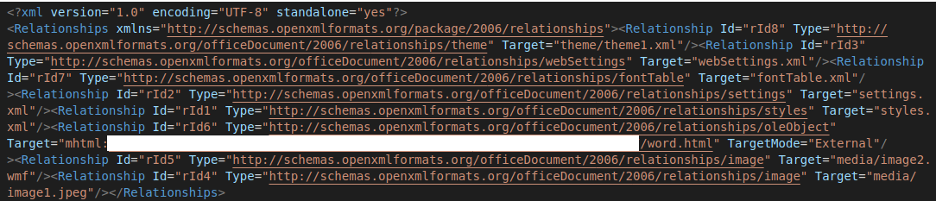
This file contains the instructions for the next step: downloading a CAB file. From there, a DLL will be extracted and run, achieving remote code execution.
Mitigating CVE-2021-40444
Microsoft has already issued security updates to address this vulnerability. You can find all the relevant information you need here. Around the office, make sure your users are paying attention to warnings triggered by Office products. Make sure they're treating any file downloaded from the internet as dangerous, and not opening any files from unknown sources.
But how do you know if your own network is vulnerable? That's easy. Just download a free, two-week trial of Keysight Threat Simulator and safely test your own network's defenses. A breach and attack simluation platform, Threat Simulator makes it easy to continuously assess your security posture, pinpoint vulnerabilities, and prevent tool drift.
We've already released multiple audits relating to CVE-2021-40444, so you can literally see if you're vulnerable right now. Of course, the bad guys never stop changing tactics. That’s why it’s our job to stay a step ahead. We're always tracking malware variants as they evolve over time, and releasing new audits and assessments to cover latest emerging tactics, techniques, and procedures (TTPs).
Be sure to watch this space for future updates, and don’t hesitate to reach out to our Security Solutions Team if you have any questions. We’re always happy to help you stay protected!
Happy threat hunting!