
Threat Simulator Helps Enterprises Realize the Vision of SecOps
By Yong Zhou |
I recently ran into an old friend virtually (what do you expect nowadays?!). He was my customer back in the day, responsible for security engineering/testing at a large financial firm. Now he is the CISO at a mid-size enterprise, leading the charge to establish enterprise SecOps to fend off the increasing cyberattacks, protect the critical data (both its own and the customers), and deliver services for its businesses. Our conversation quickly turned into the essentials of enterprise SecOps. Following is a synopsis and how Keysight’s Threat Simulator solves some of the challenges:
First and foremost, what is SecOps?
SecOps is the combination of cultural philosophies, practices, and tools that increases an organization’s ability to deliver security and services at high velocity: evolving and improving an organization’s security posture at a faster pace than organizations using traditional security and infrastructure management processes. This speed enables organizations to better serve their customers and compete more effectively.
In short, SecOps is a vision, not a product or a product list! Here are some fundamentals we need to address:
- “Security is a process, not a product”
This quote was from Bruce Schneier in his May 2000 newsletter, but it still holds true today and in the foreseeable future. According to Gartner, there are four stages of an adaptive security architecture a SecOps team is constantly working on: Predict, Prevent, Detect, and Respond. At the core of these stages to “glue” the whole process together is Continuous Visibility and Assessment.
Keysight’s Threat Simulator, as a breach and attack simulation solution, provides continuous security assessments of both network and host-based security controls.
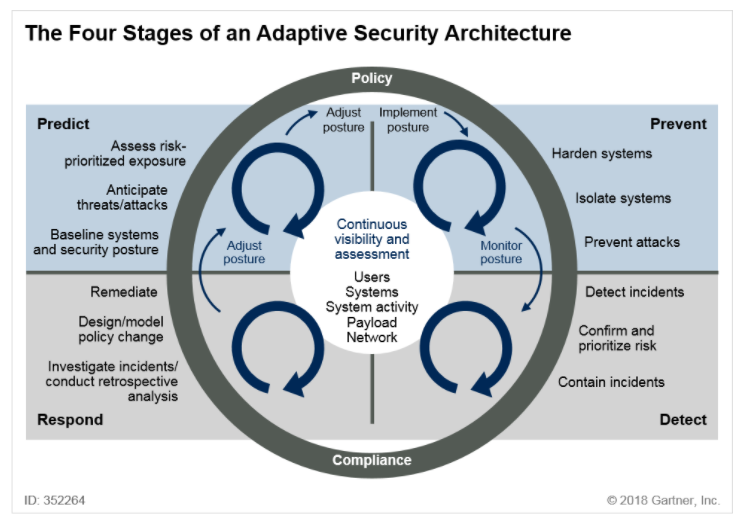
Source: Gartner, “OT Security Best Practices,” Ruggero Contu, Lawrence Orans, Refreshed 5 March 2020, Published 14 September 2018
- Cybersecurity: Advantage, the Bad Guys?
Malicious actors possess an asymmetric advantage over cyber defenders because they only need to be right ONCE! But there are ways to level the playing field and stay ahead to be prepared.
“Attack yourself before they do.” This is not just a catchphrase, but a general practice made it possible by Threat Simulator.
- Learn Attack Patterns and Techniques
Even though the tasks of defending off ever-increasing cyberattacks look daunting, there are similar attack patterns and underlying techniques SecOps teams can learn and prepare for.
The Threat Simulator security audits support various commonly used attack techniques per the MITRE AAT&CK framework. It’s kill-chain assessments emulate the full life cycles of real-world advanced persistent threats (APTs), providing excellent purple-team training exercises to set up and optimize the process of the incident detection and response by SecOps.
- Automation, Automation, and Automation!
Automation enhances enterprise security maturity with practiced processes in place for security incidents.
Threat Simulator as the breach and attack simulation solution is fully automated from agent deployment and detection to scheduled security assessments, and integration with SIEM, SOAR (coming soon), and workflow management via a ReST API.
- Streamline the Compliance Effort
Compliance has traditionally been a taxing endeavor to businesses, but it can be as simple as running an assessment and report.
Threat Simulator assessments library consists of pre-built suites covering web application security, corporate edge security, URL security, data filtering security, and many more. Threat Simulator also provides executive reports and drift analysis reports (coming soon) with quick summaries and clear guidance for compliance.
In summary, Threat Simulator enables users to realize the vision of enterprise SecOps by:
- Measuring cybersecurity efficacy and identifying gaps
- Providing clear recommendations to prioritize and/or remediate the gaps
- Validating security continuously to maintain and improve the overall security posture in a fully automated fashion
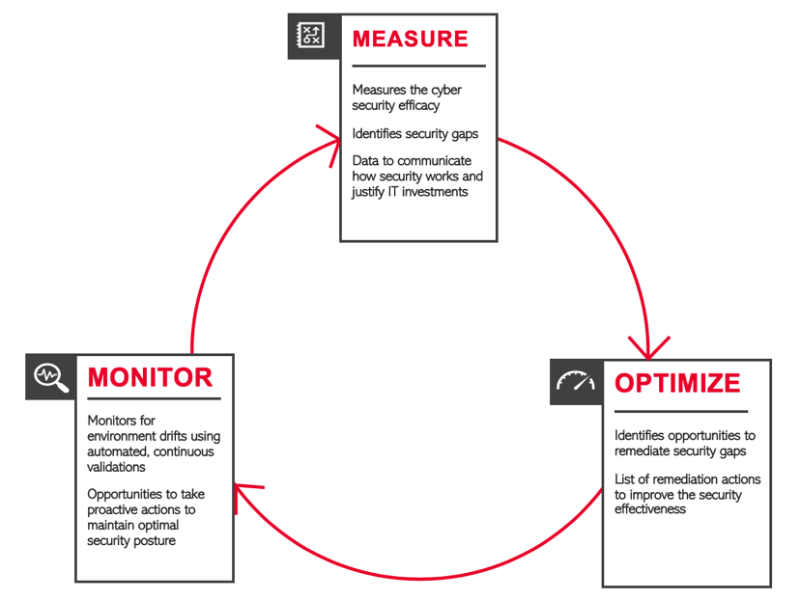
Security is never static. Continuously assessing your security controls proactively using a solution like Treat Simulator will help to improve the security maturity of your enterprise SecOps. Give Threat Simulator a (free) try today.