
Simple Advanced Persistent Threat Emulation with BreakingPoint Attack Campaigns-Part 1
Emulating an advanced persistent threat (APT) along with high-performance realistic traffic is a challenge regardless of the tools and methods used. BreakingPoint offers the capability to easily generate a high volume of realistic traffic along with security attacks, while also providing the flexibility for custom made, advanced configurations. While leveraging the full benefits of this flexibility, highly complex test scenarios are possible, typically the work factor is also proportional. Therefore, we are always looking at how to make highly advanced test scenarios not only possible but greatly simplified.
With APTs on the rise, the need to emulate such highly complex tests is greater than ever. So, what are the available options?
Keysight’s Application and Threat Intelligence (ATI) team builds realistic application and attack content for a variety of Keysight’s products. With this high level of expertise comes great responsibility as well. Consequently, the ATI team took up the challenge for creating APT test scenarios and has now released a new type of attack class in BreakingPoint known as “Attack Campaigns”.
Attack Campaigns closely resemble real-world APT malware-based attacks. The goal is to deliver a step-by-step representation of the real kill-chain (to the extent possible) based on strikes, all grouped in a strike list. Such campaigns are part of ATI StrikePack updates, available with your current ATI subscription service.
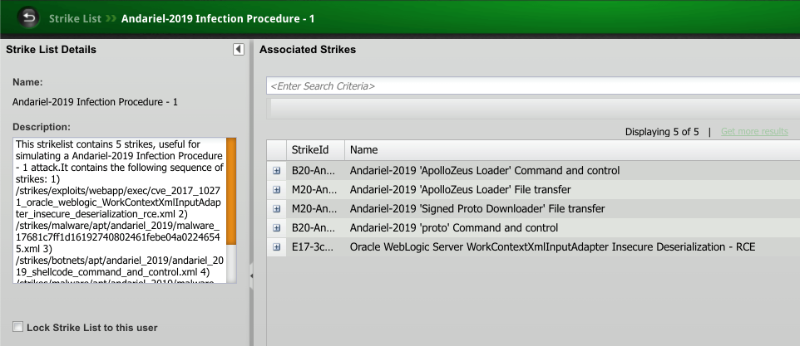
ATTACK CAMPAIGN STRUCTURE
To maximize the ways BreakingPoint users can benefit from the new content, the StrikePack updates will include, besides the StrikeLists of the kill-chains themselves, the new strikes that compose the kill-chain, and canned tests for each of the attack campaigns.
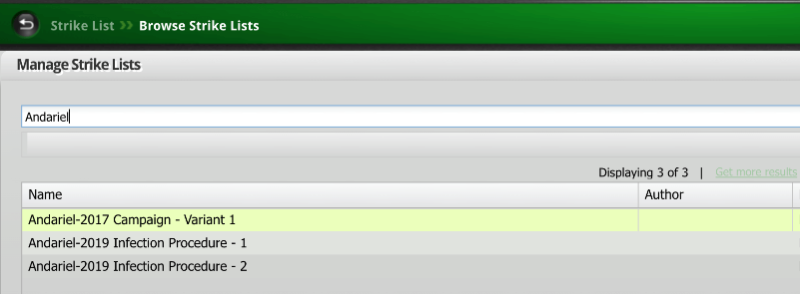
Why more StrikeLists for a single Campaign?
Each campaign might have quite involved branching logic that results in numerous permutations. Each step might have multiple options—different malware samples, different droppers, different CnC traffic, etc. Each StrikeList is one particular path of a known permutation of the campaign, not all that are possible. Therefore, another important aspect is the fact that the strikes comprising an attack campaign are highly contextual and some of the strikes are relevant when executed in the respective attack campaign context.
Why are there multiple tests for each Campaign?
The need for a canned test is to make the test more accurate and easier to use and repeat. It sets a few fields outside of the StrikeList that are required for it to look more like it would in a real scenario. For example, it sets the component to only run one strike at a time or it sets the Network Neighborhood to a small IP pool that has a single client and server IP. The user can then clone this canned test and edit it to their choosing to make it more relevant to their network.
Obviously, this can be only the starting point as users can always create new tests using the canned resources and augment it with real application traffic (to emulate the legitimate production traffic), or add distributed denial of service (DDoS) components for a smokescreen to camouflage the APT. Furthermore, to increase the detection difficulty, obfuscation techniques can be added by applying custom evasions.
The new advanced Attack Campaign scenarios further extend BreakingPoint’s capabilities in an easy to use manner. We’ll also provide a detailed dissection of the first Attack Campaigns in a second blog on this topic.
LEVERAGE SUBSCRIPTION SERVICE TO STAY AHEAD OF ATTACKS
Ixia's Application and Threat Intelligence (ATI) Subscription provides daily malware and bi-weekly updates of the latest application protocols and vulnerabilities for use with Ixia test platforms. The ATI Research Center continuously monitors threats as they appear in the wild. Customers of BreakingPoint have now access to attack campaigns for different advanced persistent threats, allowing them to test their currently deployed security controls’ ability to detect or block such attacks.